Businesses of all scales and industries see cybersecurity as an essential part of their operations and a foundation of their stability. A systematic approach to cybersecurity implies understanding of its goals and objectives, and a wise choice of tools.
Оne of the main pillars of a business security system is cyber threat intelligence (CTI). It’s the process of gathering, analyzing, and implementing information about current and potential cyber threats. By providing actionable insights, CTI enables organizations to stay ahead of adversaries and build resilient defenses.
The data can be collected from a number of sources including threat databases, public reports and research, dark web forums and social media. Certainly, the most preferable are professional threat intelligence services that provide fresh, organized, verified, enriched, ready-to-use data.
Why is Cyber Threat Intelligence Important for Business
Reacting to threats and attacks is not enough, even when reactions are fast and forceful. Prevention is better than response, because if you are responding then the damage is already done. And CTI is all about prevention and proactiveness. It provides:
· Early Detection of Vulnerabilities: Identify weaknesses in company’s infrastructure before they can be exploited.
· Threat Actor Profiling: Know your adversaries, predict their actions and focus your resources on the most relevant threats.
· Real-Time Alerts: Receiving prompt notifications about emerging threats enables security teams to respond swiftly and effectively.
How Treat Intelligence Impacts Company’s Efficiency
Cyber security tools are not something you just implement for the sake of it, to be trendy and keep up to the Jobses. They improve your business’ sustainability; help reduce costs and grow profits. How can CTI actually help with all that?
1. Informed Decision-Making
Up-to-date relevant information is needed to make strategic and tactical decisions with confidence. CTI enables organizations to run risk assessment and prioritization and allocate resources more effectively. Besides, CTI facilitates clear and concise communication of risks to stakeholders, board members, employees, and customers.
2. Improved Incident Response
CTI plays a crucial role in enhancing incident response capabilities. The speed and efficiency of the response can make a significant difference in mitigating the impact.
By understanding the tactics and approaches of threat actors, organizations can implement targeted containment measures. This reduces the spread and danger of the attack.
What if an incident has already happened? CTI is also a means of post-incident investigations that help prevent problems in the future. Intelligence provides a ton of invaluable information on threat actor’s Tactics, Techniques, and Procedures arming security experts for further protection enforcement.
3. Compliance
Many regulations, such as UN’s the General Data Protection Regulation (GDPR) and the California Consumer Privacy Act (CCPA), require organizations to demonstrate robust cybersecurity practices. Certain industries, such as finance and healthcare, have stringent regulations. Non-compliance can result in hefty fines, legal consequences, and reputational damage.
CTI helps companies meet regulatory requirements and align with specific security standards. Besides, threat investigation assists in preparing for audits by documenting security measures and demonstrating proactive risk management.
4. Competitive Advantage
Proactively protecting customer data and communicating their cybersecurity efforts is a good strategy for a business to build trust and loyalty. On the other hand, a strong security posture reduces the likelihood of incidents that could harm the company’s reputation. We have all seen too many cases when businesses that experience data breaches face long-term reputational damage.
TI Lookup: Comprehensive Threat Intelligence Service
Threat Intelligence Lookup by ANY.RUN is a worthy example of a CTI system that provides a cybersecurity solution for small businesses as well as larger companies.
The service delivers real-time and historical data on the Indicators of Compromise — objects, events, and activities in the network that may indicate a system compromise. The data is contextually enriched and illustrated by Interactive Sandbox sessions where security experts detonate malware and view it in action in emulated environment.
TI Lookup connects threats to known attack campaigns or malware families. Users can check the reputation of URLs, IPs, or files to determine their level of maliciousness. Malware names, IP addresses, suspicious links, domains, file names, hashes, and other entities can be used as search queries. Complex search requests can be made combining several parameters.
Here is an example of a search performed via TI Lookup:
threatName:”phishing” AND submissionCountry:”CA” NOT taskType:”url”
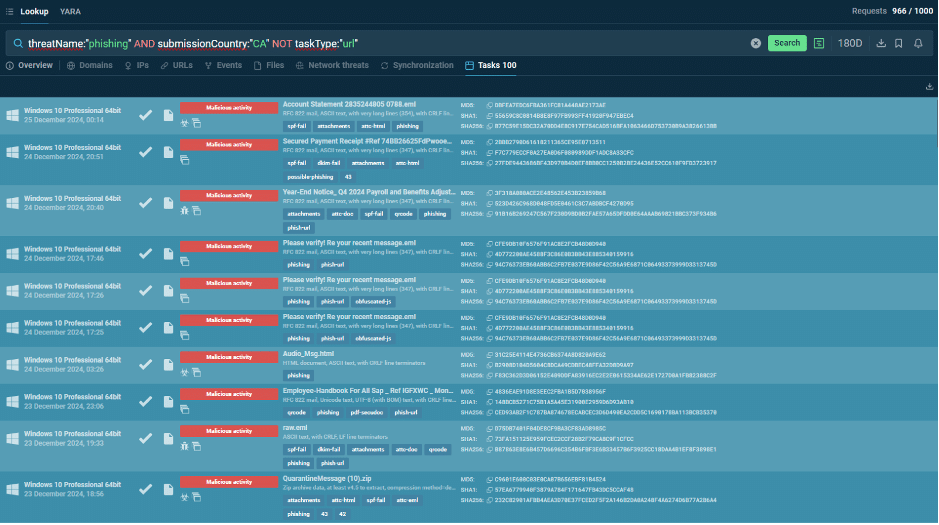
Search results illustrate the current situation with phishing attack targeting Canadian users
As a result, we see a selection of public analysis sessions run in ANY.RUN’s Interactive Sandbox by users from Canada. These are the sessions that include phishing documents, emails, and other types of content, but not URLs. By clicking any item on the list, you can view the analysis session in the sandbox.
Try TI Lookup with 50 free requests → |

