There’s no arguing that software engineer and inventor Dr. Siyang Luo is a bona fide expert in the technologies that have come to define the modern era of technological progress, such as AI and Big Data.
Add to that a dedicated interest in and study of cybersecurity, a field that has only grown increasingly complex as attacks against organizations and individuals have become more intrusive and malignant.
Currently the Young Managing Director of Shanghai Infortech Software Development Co., Ltd., Dr. Luo has applied his expertise to numerous patents, research papers, and professional collaborations. He is also the Director of the Seventh Council of the China Computer Industry Association.
While we didn’t have the time to cover the full breadth of Dr. Luo’s work in our interview, we did have the opportunity to discuss multiple patents and a cutting-edge cybersecurity system that Dr. Luo has pioneered.
Hello, thanks for joining us. Can you tell our readers where you work and what you focus on?
I work at Shanghai Infortech Software Development Co., Ltd., a high-tech enterprise centered on the Chinese mainland, providing IT solutions and services to Southeast Asia. Founded in 1998, the company is headquartered in Shanghai, with branches in Qingdao, Guangzhou, Kuala Lumpur, and other regions. In 2012, for the rapid development of the company, it formally introduced the investment of Japanese joint-stock company NTT DATA, a Global 500 company, to break into the international market more quickly.
So far, it has provided corresponding products and solutions for dozens of well-known enterprises in seven countries. Important clients include FamilyMart, Fujitsu, Sumitomo Mitsui Banking Corporation, Dicos, Qdama (Qiandama), AEON CHINA, Canon (Suzhou), etc. Its business scope has also extended to Malaysia, Kazakhstan, Vietnam, and other regions in Southeast Asia as well as Hawaii in the United States.
Readers can find more details on our company homepage.
As for my own work, I mainly focus on retail industry software system development, data science, and network security. I’ve secured many patents related to these fields.
To what degree would you say your education prepared you for advanced real-world AI and Big Data work?
My college education spanned both China and the US. My US college education experience was more academic and theoretical, which built my solid skills and knowledge background in AI and Big Data work.
Comparatively, my college education experience in China was more practical, which helped me put my knowledge and skills to real use. Also, I am currently a managing director of a multinational tech company, so my multinational experience has helped me to apply real-world AI and Big Data in different countries and regions effectively.
Can you elaborate on your AI checkout system? What are some of the key benefits?
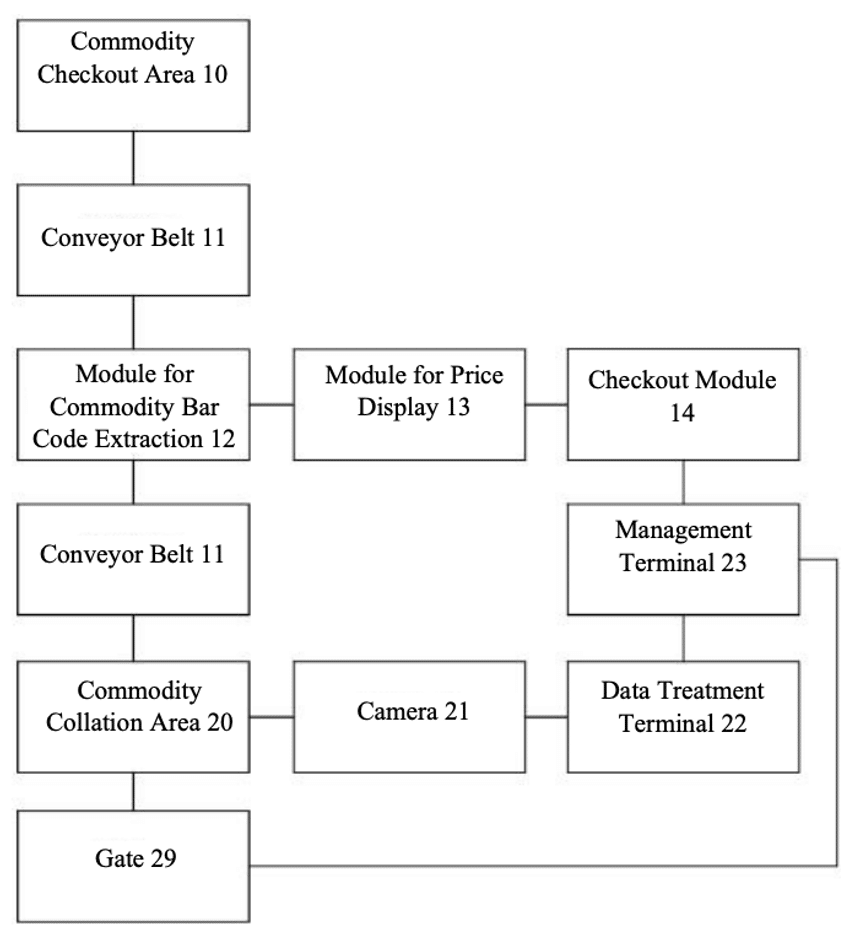
This invention provides an Artificial Intelligent Checkout System for supermarkets, including the checkout area, which consists of the conveyor belt, the module for barcode extraction, the module for price display, and the checkout module.
After customers place the products they are going to purchase on the conveyor belt, the conveyor belt will send the products to the working area of the module for barcode extraction, and then send the products to the collation area after the barcode extraction is finished.
From there, the information extracted from the barcodes is sent to the price display, which tallies everything up. The checkout module acquires customers’ payment codes through the scanning device and fulfills the checkout. The commodity collation area is equipped with a gate that opens after the customers finish the checkout.
This invention can handle the checkout process at supermarkets automatically, without human involvement, saving manpower.
What was your entry point to cybersecurity, and do you see this entry point as feasible for other AI/Big Data tech professionals?
I got to do research in cybersecurity during grad school, and that was how I got started with cybersecurity. A while ago, I published a thesis in an international journal: “Research on the Application of Network Security Situational Awareness System based on Big Data in Network Security Management.”
Under the development background of information technology such as big data, internet technology, and cloud computing, internet technology has been widely used in people’s lives and work, and the forms and means of network attacks are becoming more and more diversified.
In my thesis, I designed a network security situational awareness system. The effective use of this network security situational awareness system can further improve the positioning and processing effect of internal and network attack sources, effectively evaluate the impact and understand the intention according to the macro perspective, provide corresponding decision support, improve the network’s anti-risk ability, and meet the requirements of current network security management.
Especially in recent years, with the increase of mining software, computer viruses are even more rampant, severely affecting global network security. Simply adopting a single security protection method cannot satisfy the relevant requirements of network security management. Accordingly, it is necessary to build a unified network security management system and comprehensively evaluate and analyze network security logs so as to upgrade the quality of network security management.
In such cases, the significance of applying a situational awareness system becomes more and more evident. A situational awareness system is a detection system based on internet technology, which can comprehensively and dynamically predict network security risks and enhance the ability of responsible parties to identify and respond to security risks by employing Big Data and related security technologies.
During an attack, a situational awareness application can detect the purpose and means of the attacker so as to deeply analyze the cause of system damage.
How can Big Data transform cybersecurity going forward?
A while ago, I patented an invention called “Protecting Method and Platform of Cyber Security Based on Big Data.”
The method and platform for network security protection based on big data provided in this patent involve the field of network security technology. In this patent, the OS fingerprint of the target virtual applications is replaced with the OS target fingerprint when the request for the OS fingerprint is received.
Secondly, if the target-attack device is detected to recognize the target virtual applications running on the virtual computer, the history data of the target is obtained from the first target database. Then, whether the target virtual applications will be identified as running on the virtual machine in the next attack can be determined based on the target history data. Finally, if the target virtual applications are identified as running on the virtual machine, the OS target fingerprint will be updated based on the new physical machine OS fingerprint.
Using this method, existing network security technology can be drastically improved.
Stepping away from the technical details for a moment, we’d like to hear about some of the notable professionals you’ve collaborated with
Probably my most notable collaboration was with Dr. Defeng Sun, the Head and Chair Professor of Applied Optimization and Operations Research at the Department of Applied Mathematics at The Hong Kong Polytechnic University. Also, he is a fellow of SIAM and CSIAM. It was a pleasure working with such a highly-regarded individual, and I learned a great deal from him.
Before we finish up, is there anything you can tell us about the work you’re doing at the moment?
I am currently finishing my SCI paper titled, “Spatial Graph Attention Network-based Spatio-temporal Flow Prediction for Retail Big Data.” It will be published in a top-tier international journal, most likely IEEE Access.
I’m very excited to publish this piece, and I’m looking forward to seeing the response following publication.